7cric
Online Betting App & Guides
Get in the game with 7cric – India’s best online betting app and site. With competitive odds across 30,000+ markets, it’s the go-to platform for online cricket betting, sports and casino gaming.
Best Betting App in India
The Best Online Betting Site in India
7cric is the best betting app in India and the most trusted online casino site, licensed by the globally recognized iGaming licenses and one of the fastest growing online casinos in India that offers over 4,000 casino games available.

Hot Promotions
7cric offers huge bonus for new and existing members.

Tons of Games
- Cricket & Sports
- Live Casino
- Online Slots
- Card Games

Secured Payments
From UPI, PayTM, PhonePe, BHIM, to local bank transfers, we have prepared the most secured payments for every transactions.

Cross Platform
Available on website and mobile app, 7cric offers the most flexibilities in online betting. Bet on-the-go anywhere.

Flexible Betting
Choose from over 4,000 games. Live casino, slots, sports and cricket betting, betting exchange, card games, and more.
Through our extensive gaming library and secure, legal operational standards, 7cric provides a premier online betting and casino experience catered specifically to the Indian market. Our growth and popularity among players demonstrates our success in offering an unparalleled range of betting options tailored for Indian gamers seeking a high-quality digital gambling platform. As the gaming landscape continues to expand in India, 7cric is poised to remain an attractive choice for players looking for variety, safety and convenience.
Powered by Saba Sports & BetB2B
Online Cricket Betting & Sports
7cric offers online cricket betting and other major sports. Indian players will find an extensive array of cricket betting markets, covering national and international leagues. With competitive cricket odds and a wide variety of bet types across top sporting events, 7cric provides a premier destination for fans seeking to wager on their favorite sports online.
Real-Time Betting
Bet on-the-go on future and on-going matches.
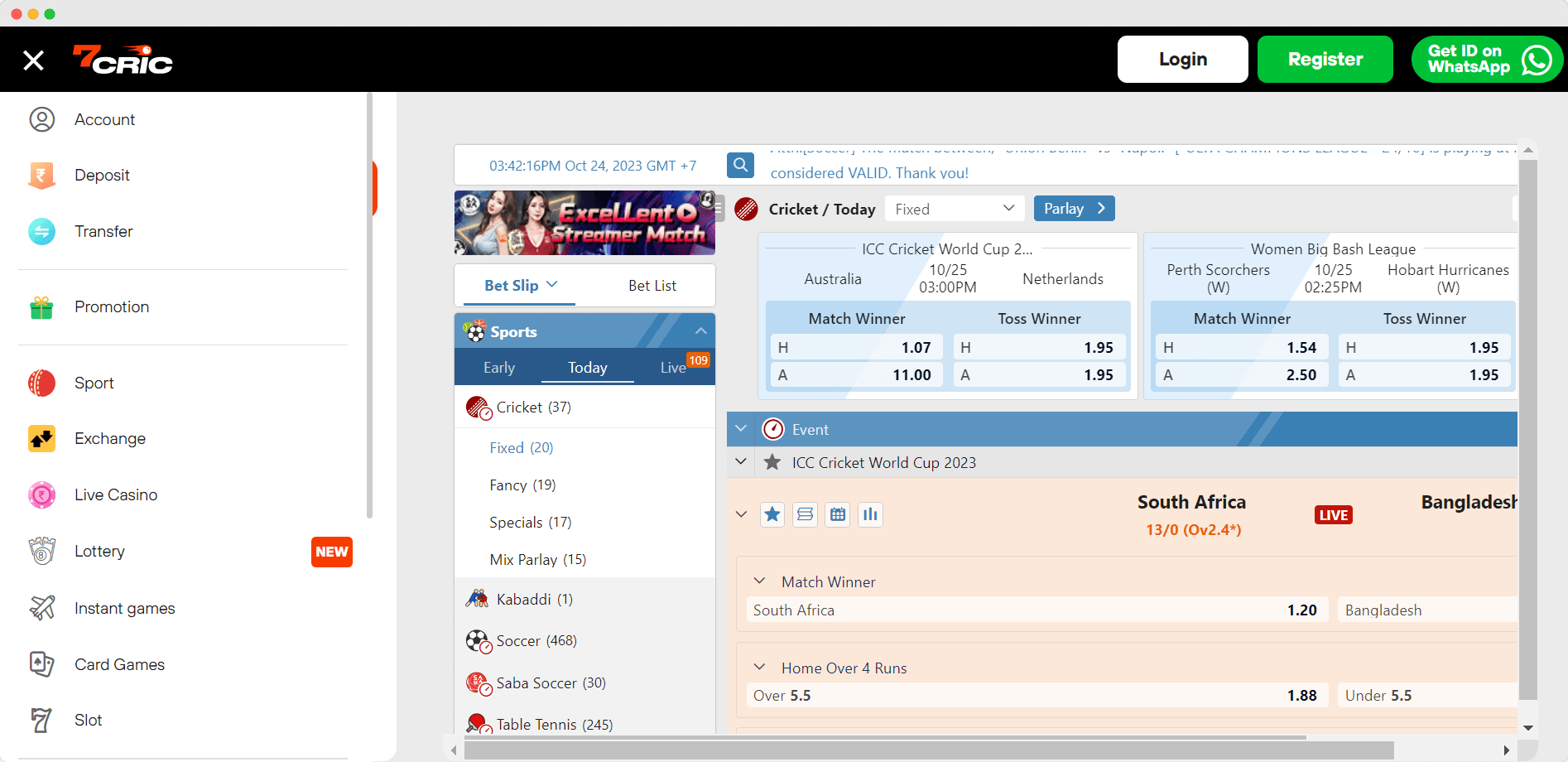
Live Scores
- Bet in Real-Time
- Betting Exchange
- Live Statistics
- Match Predictions

Live Scores
Live cricket scores feature is available in one spot for you to analyze the current matches and anticipate the upcoming games.

Today Match Prediction
Who will win today? 7cric provides comprehensive match predictions to help you analyze the game and bet on the right team.

Surprising Promotions
While betting on cricket or watching the matches, claim the promotions that will be appeared surprisingly on your bet account.
For the ultimate online cricket betting and sports wagering experience tailored for Indian fans, look no further than 7cric. Powered by leading iGaming providers Saba Sports and BetB2B, 7cric offers unmatched variety across cricket and other major sports.
Find the best cricket odds on domestic tournaments like IPL as well as international competitions. With an intuitive interface, flexible payment options, and 24/7 support, 7cric provides a feature-rich platform enabling Indian bettors to safely wager on their favorite cricket matches and sporting events. As the go-to sportsbook for Indian players, 7cric delivers the perfect blend of cricket and sports betting excitement.
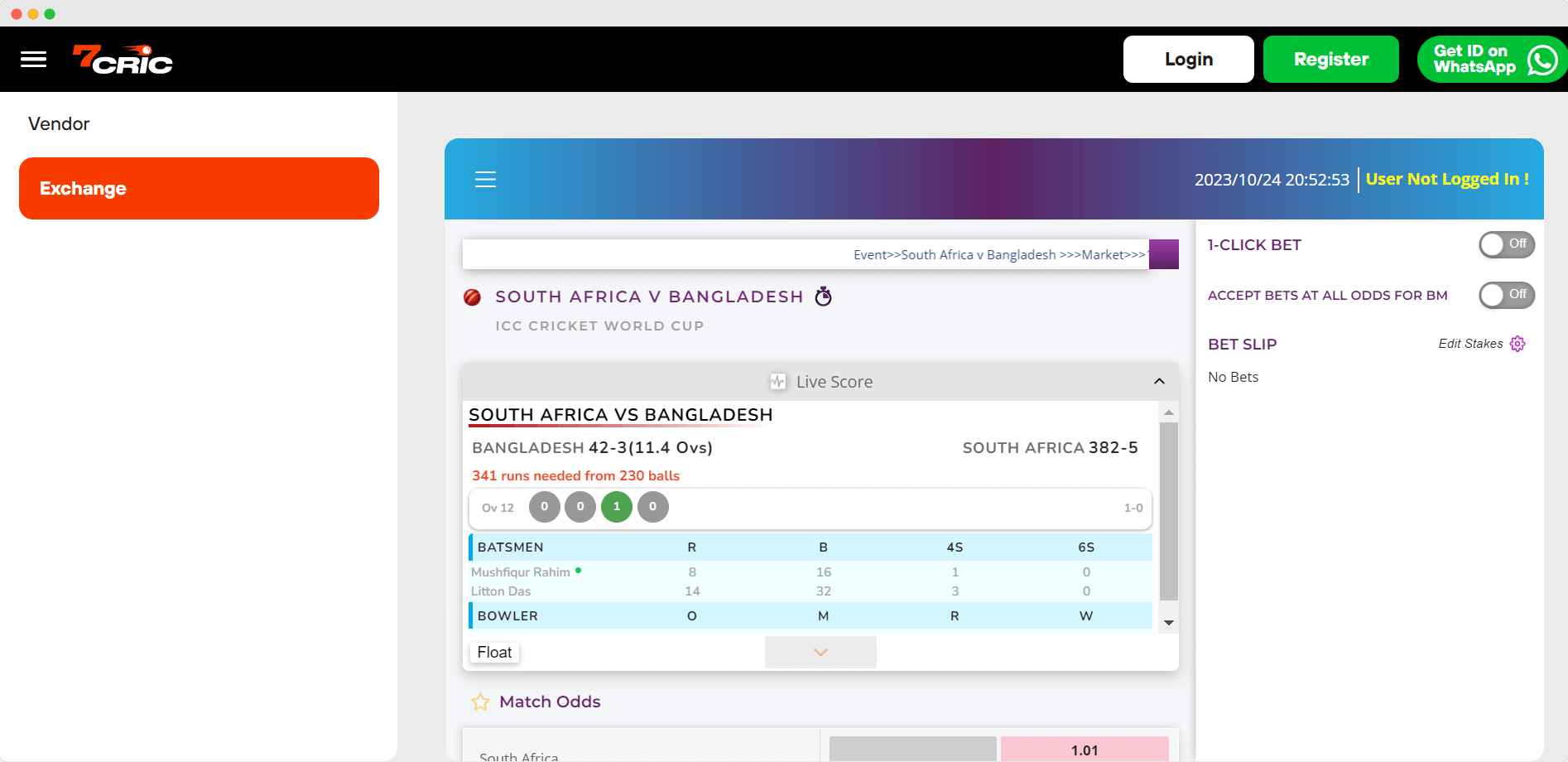
Betting Exchange
Cricket Betting Exchange & Sports
As India’s top betting exchange platform, 7cric empowers customers with an interactive marketplace to trade bets on discrete events in real-time.
Unlike traditional bookmakers, 7cric allows gamblers to both buy and sell outcomes with optimal odds.
By charging modest commissions on winnings rather than inefficient odds, 7cric offers Indian players the fairest and most transparent betting exchange environment. With dynamic betting lines that respond to market activity, bettors can hedge positions to minimize risk and maximize profitability across events.
For an unparalleled betting exchange experience tailored to Indian punters, 7cric is the platform of choice. With its user-driven odds and real-time trading, 7cric delivers more control, engagement and value than any other Indian betting exchange.
Live Casino
Live Casino by 7cric — The Best Live Casino Online
7cric’s Live Casino stands out as the pinnacle of online gaming experiences, offering an unparalleled fusion of traditional casino play and modern technology.

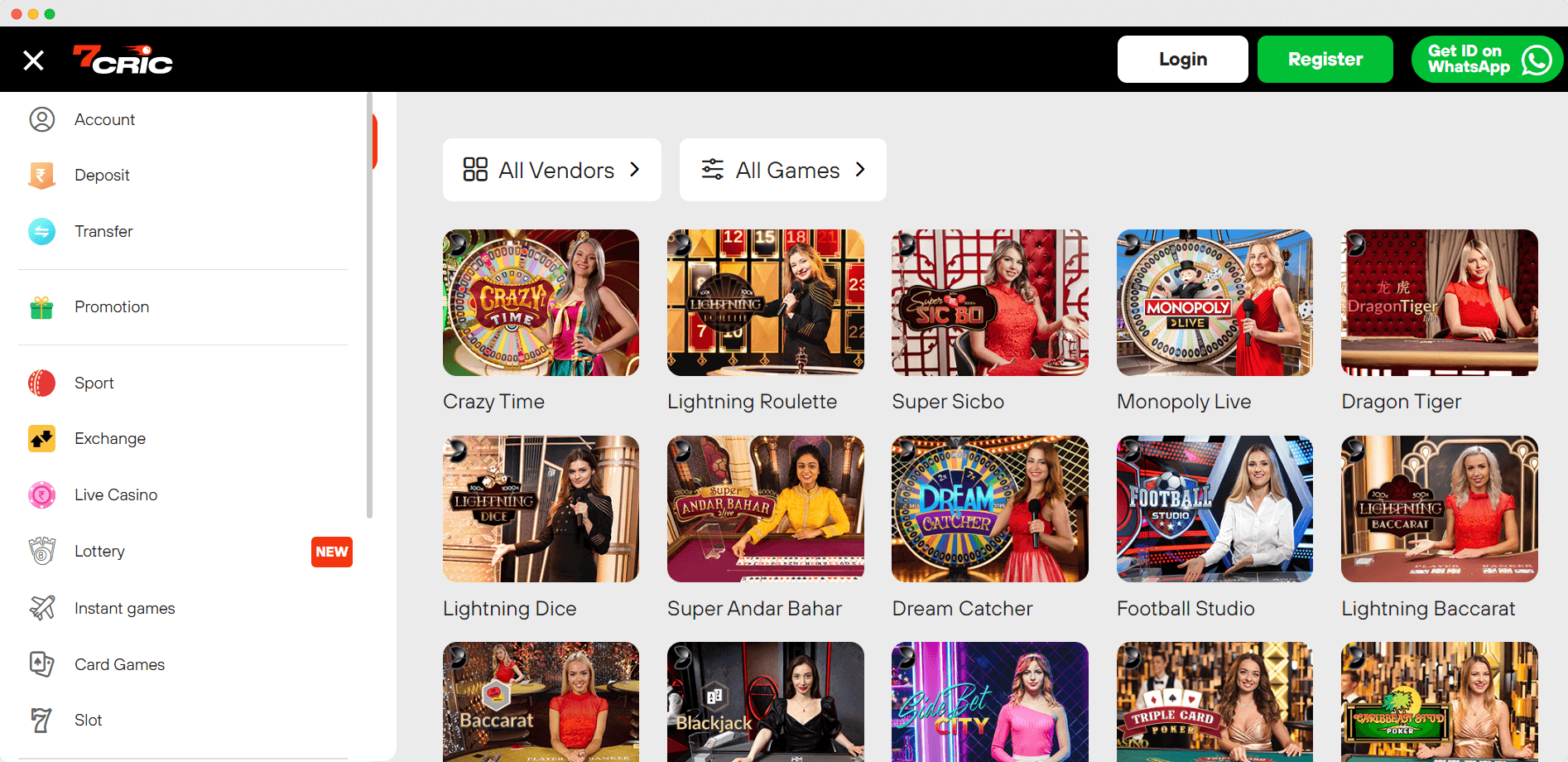
Designed to recreate the ambiance of a physical casino, it provides players with real-time interactions, live dealers, and high-definition streaming. Whether it’s the spin of the roulette wheel, the thrill of blackjack, or the strategy of poker, 7cric’s Live Casino brings the authenticity of a brick-and-mortar casino right to your screen. With its seamless interface, diverse game offerings, and professional dealers, 7cric has undoubtedly established itself as the best live casino online.
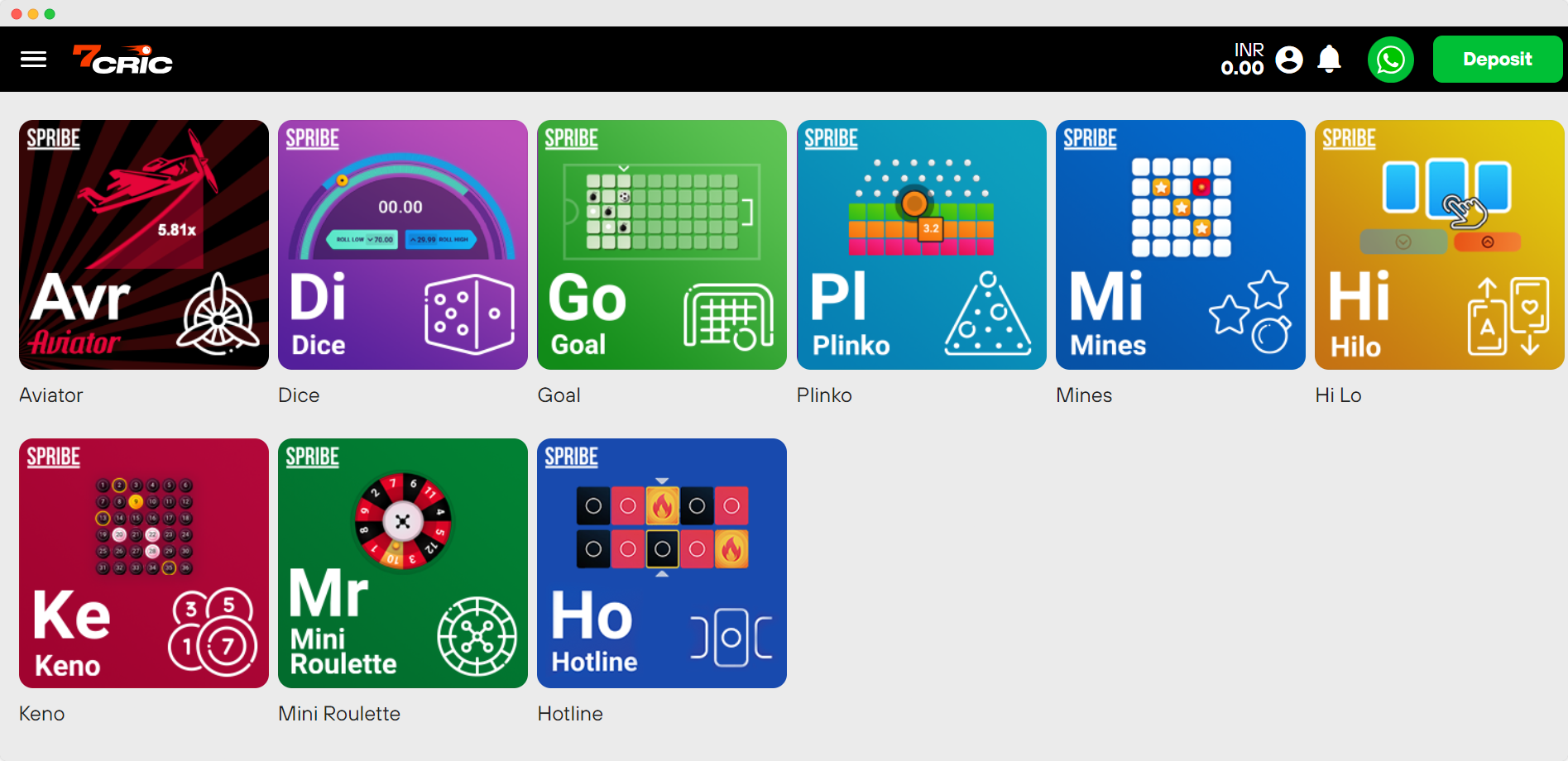
Instant Games
Play the Most Popular Crash Gambling Games
From Aviator to the classic Keno, play the most popular instant or crash gambling games and win big money!
7cric has become the go-to destination for casino enthusiasts seeking a diverse and engaging gaming experience. Offering a vast array of the most popular instant casino games, 7cric ensures that players are always spoilt for choice. From classic slots and progressive jackpots to table games and specialty options, every game is designed with high-quality graphics, immersive sound effects, and user-friendly interfaces. The platform’s commitment to regularly updating its game library means that players can always expect fresh content and the latest gaming trends. For those seeking instant entertainment and the chance to win big, 7cric stands out as the premier choice.




We’re 7cric, your go-to app for online betting in India. We make cricket betting a breeze, offer diverse sports wagering, and spice things up with our online casino. We’ve got you covered whether you’re an IPL die-hard or a football fanatic.
We’re not just about sports, our casino ensures a thrilling experience for everyone. We’re leading the way in the Indian online betting scene and we’re dedicated to enhancing your betting experience.
Join us and plunge into the exciting world of online betting!
- 7cric is a leading online betting platform in India that offers a wide range of betting choices and a user-friendly interface.
- The 7cric app has played a crucial role in the rise and acceptance of online betting apps in India, providing freedom and diversity in betting options.
- The platform provides a seamless cricket betting experience, a wide range of online casino games, and allows for instant withdrawals.
- 7cric enhances the betting experience with features like accurate match predictions, betting in exchange, and bet exchange, empowering bettors to be more strategic and successful in their endeavors.
7cric: Leading the Online Betting Landscape in India
In the booming online betting scene in India, 7cric has established itself as a frontrunner.
It’s not just a betting app, but a complete platform that caters to the taste of Indian bettors with ease of use, accurate forecasts, and a wide array of betting choices.
We’ll look at how 7cric, with its impressive features and secure platform, has become the top choice for online betting enthusiasts.
The Rise of Online Betting in India
We’re seeing an undeniable surge in online betting in India, and at the forefront is 7cric, setting the pace with its comprehensive platform.
Catering to Indian betting enthusiasts, it’s not just about cricket; there’s a whole spectrum of sports and casino games to wager on.
Let’s explore this revolution in online betting guides, navigating through what sets 7cric apart in the bustling landscape of Indian betting sites.
Embracing the Online Betting App Revolution
As we’ve seen, a significant number of Indian bettors have embraced the online betting app revolution, with 7cric leading the charge.
This best betting app in India offers a liberating, user-friendly platform for online cricket betting.
It’s no wonder that by offering such freedom and diversity, 7cric app has played a crucial role in the rise and acceptance of online betting apps in India.
Navigating through Top Betting Sites in India
Over time, we’ve navigated through the top betting sites in India and 7cric clearly stands out, leading the online betting landscape with its diverse offerings and user-centric approach.
It’s the best betting app with instant withdrawal, making it a favorite among cricket betting app enthusiasts.
7cric: The Best Betting App in India
Let’s now turn our attention to why 7cric stands out as the best betting app in India.
We’ll explore the features that set it apart and compare it with other online betting sites.
In doing so, we aim to highlight the edge that 7cric holds in the market.
Features that Set 7cric Apart as the Best Betting App
We’ve identified several standout features that make 7cric the top choice for online betting in India.
As the best betting app, 7cric liberates users with a seamless cricket betting experience, diverse online casino games, and instant withdrawals.
Its user-friendly interface and accurate match predictions further enhance the online betting experience.
Now, let’s transition to comparing online betting sites, and further explore 7cric’s edge.
Comparing Online Betting Sites: 7cric’s Edge
In comparing numerous online betting sites, we can confidently say that 7cric holds a significant edge in the Indian market. Here’s why:
- User-Friendly: 7cric’s betting app is intuitive and easy to navigate.
- Diverse Betting Options: From cricket to casino, it’s all available.
- Accurate Predictions: Enhance your betting strategy with reliable forecasts.
- Security & Quick Withdrawal: We ensure your betting is safe and winnings accessible.
Mastering Online Cricket Betting with 7cric
Let’s now turn our attention to how one can master online cricket betting with 7cric.
We’ll be looking at how today’s match predictions can enhance betting strategies, the pros and cons of online betting apps versus traditional platforms, and the role of online cricket ID in modern betting.
These aspects are crucial in understanding the nuances of betting in the digital age.
Today Match Prediction: Enhancing Online Cricket Betting Strategies
We’re enhancing our cricket betting strategies on 7cric with the help of accurate ‘Today Match Predictions‘. This plays a vital role in making our game bet online more exciting and profitable.
- Today match prediction helps us anticipate the potential outcome, giving us an edge over other bettors.
- Online cricket betting becomes more engaging and strategic, with match predictions guiding our betting choices.
- Betting tips based on match predictions enhance our understanding of match odds, enabling us to make informed wagers.
- Our betting strategies become more refined and effective, leading to higher chances of winning and ultimate liberation.
In essence, ‘Today Match Predictions’ not only enhance our online cricket betting experience but also empower us to be more strategic and successful in our endeavors.
Online Cricket Betting Apps vs. Traditional Betting Platforms
Moving on from predictions, mastering online cricket betting on 7cric, we’ll compare how betting apps like 7cric offer us distinct advantages over traditional betting platforms.
With 7cric, you’re no longer bound by location or time. We can bet in exchange for real-time cricket betting odds, anytime, anywhere. This freedom is something traditional betting sites can’t match.
Furthermore, the online cricket id feature provides a secure, personalized betting experience. For IPL betting, 7cric gives us the power to bet live during matches, empowering us to make informed decisions based on the game’s progress.
The Importance of Online Cricket ID in Modern Betting
In our journey to master online cricket betting with 7cric, our online cricket ID’s significance becomes increasingly apparent, transforming the way we approach modern betting.
This cricket betting ID isn’t just a profile; it’s our passport to freedom and potential monetary gains.
- Privacy: Our ID ensures anonymity, liberating us from societal judgments.
- Access: With it, we can enter the exciting world of cricket and football betting.
- Efficiency: We receive personalized football betting tips, speeding up our decision-making process.
- Flexibility: It allows us to participate in a bet exchange, providing an opportunity to maximize our returns.
In essence, our online cricket ID is our key to unlocking the full potential of 7cric, providing the freedom we yearn for in the realm of online betting.
Beyond Cricket: Expanding the Sports Betting Horizon
While we’ve established 7cric’s prowess in cricket betting, it’s time to explore other arenas.
Let’s shift our focus to the thrill of football betting and strategies that can amp up your game.
We’ll also discuss the dominance and excitement of IPL betting in India.
Football Betting on 7cric: Tips and Strategies
Beyond the realm of cricket, we’ve expanded our betting horizon to include football on 7cric, offering tips and strategies to enhance your betting experience.
- Understand the Game: Familiarize yourself with different leagues, teams, and player statistics. Knowledge is power in the betting world.
- Odds Analysis: Learn to analyze betting odds, it’s crucial in making profitable bets.
- Bankroll Management: Decide on a set amount for each wager, ensuring you don’t risk too much at once.
- Track Your Bets: Keep a record of your betting history to identify patterns and improve your strategy.
We’re here to facilitate your journey and liberate your betting potential. Now, let’s shift gears and delve into the excitement of IPL betting and its dominance in India.
The Excitement of IPL Betting and its Dominance in India
We’re diving headfirst into the thrilling world of IPL betting, a phenomenon that has truly dominated India’s sports betting scene.
This isn’t just about cricket; it’s a high-stakes, adrenaline-rushing spectacle that’s become a cultural mainstay. We’ve witnessed the surge in popularity, the charged anticipation as punters place their bets, and the sheer joy of winning.
It’s more than a game, it’s a liberating experience that breaks the monotony of everyday life.
On 7cric, we offer a platform that not only caters to IPL betting but also opens up a world of sports wagering possibilities.
But the excitement doesn’t stop at sports. As we transition into the next section, prepare to explore 7cric’s online casino: a gaming paradise in online betting.
7cric’s Online Casino: A Gaming Paradise in Online Betting
Let’s turn our attention now to 7cric’s online casino, a veritable gaming paradise for enthusiasts.
We’ll explore popular casino games and game bet online options, and help you make sense of match odds in casino games.
We’ll also guide you through seamless transactions on 7cric and share valuable tips and insights for betting enthusiasts.
Popular Casino Games and Game Bet Online Options
In our exploration of 7cric’s offerings, it’s about time we delve into the popular casino games and online betting options that make this platform a gaming paradise for Indian bettors.
- Online Slots: These games of chance are filled with fun and excitement, offering high payout ratios.
- Blackjack: A popular card game where strategy meets luck, offering a thrilling gaming experience.
- Roulette: Spin the wheel and take your chances on this classic casino game.
- Live Casino: Real-time gaming with live dealers, bringing the casino experience straight to your screen.
Each of these games brings a unique thrill, the liberation of placing a bet, and the anticipation of a big win.
Now, let’s move on to understanding match odds in casino games.
Understanding Match Odds in Casino Games
As we dive into 7cric’s online casino, it’s essential to grasp the concept of match odds, a key element that can significantly influence our betting experiences.
These odds represent the probability of an event happening in a game. They’re not just random numbers but reflect careful calculations.
Understanding these odds allows us to make informed bets, increasing our chances of success. It’s not about luck; it’s about strategy. So, whether we’re trying our hand at poker or spinning the roulette wheel, knowing the odds empowers us.
It’s about seizing control, making smart decisions, and ultimately, liberating our gaming experience. At 7cric, we’re not just playing games; we’re mastering them.
Ensuring Seamless Transactions on 7cric
We’re going to talk about how 7cric, India’s leading online betting app, ensures smooth transactions for its users.
We’ll also highlight how its features like ‘Bet in Exchange’ and ‘Bet Exchange’ enhance the betting experience.
Lastly, we’ll discuss why 7cric tops the list of best betting sites in India with instant withdrawal.
The Bet in Exchange and Bet Exchange Features
Diving into the unique features of 7cric, we’ll find the Bet in Exchange and Bet Exchange options setting the platform apart in the online betting landscape.
- Bet in Exchange: Enables live betting on ongoing matches.
- Bet Exchange: Allows users to bet against each other.
- Instant Market Update: Ensures real-time betting experience.
- Competitive Odds: Offers best betting rates.
Next, let’s delve into why 7cric tops the list of best betting sites in India with instant withdrawal.
Best Betting Sites in India with Instant Withdrawal: Why 7cric Tops the List
While many online betting sites in India offer withdrawal options, it’s 7cric that tops the list, primarily due to its instant withdrawal feature that ensures swift and hassle-free transactions.
| Betting Site | Withdrawal Speed | User Experience |
|---|---|---|
| 7cric | Instant | Excellent |
| Betway India | 24 hours | Good |
| Dafabet India | 48 hours | Fair |
We believe in liberating our users from waiting periods and providing them an uninterrupted betting adventure.
Tips and Insights for Betting Enthusiasts
In the world of online betting, making informed decisions is key to maximizing returns.
At 7cric’s online casino, we’re not just about playing the games, we’re about understanding them too.
Let’s explore how leveraging betting tips can enhance your gaming experience and potentially increase your winnings.
Leveraging Betting Tips for Informed Decisions
We’ve got valuable betting insights and tips to share, which you can leverage to make informed decisions while enjoying 7cric’s online casino and sports betting platform.
- Always bet within your budget.
- Use match predictions to guide your decisions as well as our live cricket scores.
- Engage in diverse betting options to increase winning chances.
- Always secure your earnings with timely withdrawals.
These insights liberate you to enjoy betting with confidence.
Football Betting Tips for Maximum Returns
Despite the thrill and unpredictability of football betting, we’ll share some valuable tips to maximize your returns on the 7cric platform.
We’ll guide you to wise bets, encourage diversification, and stress the importance of staying informed.
Our goal? To help you find success and liberation in the exciting world of online betting.
Now, let’s explore 7cric’s commitment to elevating the betting experience in India.
7cric’s Commitment to Elevating the Betting Experience in India
At 7cric, we’re dedicated to offering every single user an elevated betting experience in India. We’re not just providing a platform for cricket and sports betting, we’re crafting an experience that liberates you from the confines of traditional betting systems.
Here’s how we’re redefining the betting landscape:
- User-Friendly Interface: Our app’s design is straightforward, making it easy for both seasoned and novice bettors to navigate.
- Diverse Betting Options: From IPL and football to our online casino, we’ve something for every betting enthusiast.
- Accurate Predictions: We provide accurate match predictions to guide your betting decisions.
- Secure and Speedy Transactions: We guarantee secure transactions and quick withdrawals, ensuring your peace of mind.
We’re not just about providing a service, we’re about creating an experience. An experience that’s seamless, secure and liberating. This is our commitment to you. This is 7cric, India’s premier online betting platform.
Join us, and elevate your betting game to new heights. Embrace the freedom to bet how you want, when you want, and where you want. Welcome to the future of betting in India.
At 7cric, we’re passionate about offering a superior online betting experience. We’ve mastered cricket betting, broadened the sports betting horizon, and created a gaming paradise in our online casino.
We’re committed to elevating the betting landscape in India, providing a safe, seamless, and exciting platform for all your betting needs. Whether you’re a sports enthusiast or a gaming aficionado, we invite you to join us and experience the thrill of online betting with 7cric.
7cric Testimonials
What Our Happy Users Say
See what they say about 7cric. Join over thousands of 7cric’s happy players and tell the world of what you’re experiencing with 7cric. Review us on 7cric.

Latest Betting Guides & Cricket News
We regularly post helpful, high quality online betting guides and latest cricket news. Be sure to check them out.
Frequently Asked Questions
The most often asked questions about 7cric.
What is 7cric?
7cric – India’s top iGaming site offering a wide selection of gaming including online cricket betting, casino, slots, virtual sports and more.
What is the Welcome Bonus in 7cric?
In 7Cric, we offer a generous 100% to 200% Welcome Bonus for our first time users upon their first deposit.
Is 7cric real or fake?
7cric is real. 7cric is licensed and regulated by globally-recognized iGaming licenses. 7cric operates under strict regulations to ensure a safe and legal gaming environment.
Claim 200% Welcome Bonus
For a limited time, every new member can claim 200% Welcome Bonus upon registration up to ₹15,000. Read to bet?